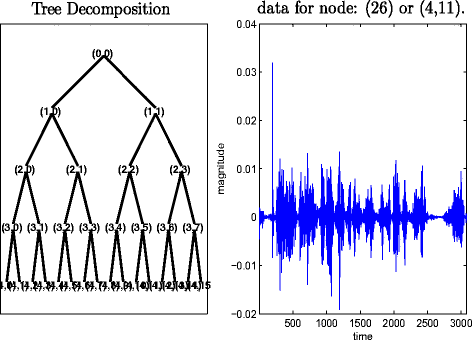
Detecting and locating digital audio forgeries based on singularity analysis with wavelet packet | SpringerLink
Lecture 4. Stegosystems for other cover objects. 4.1. Linguistic SG (SG-L) 4.2. Graphic SG (SG-G) 4.3. Internet (Network) SG (

PDF) Enhancing LSB Using Binary Message Size Encoding for High Capacity, Transparent and Secure Audio Steganography–An Innovative Approach

Detecting and locating digital audio forgeries based on singularity analysis with wavelet packet | SpringerLink
PDF) Enhancing LSB Using Binary Message Size Encoding for High Capacity, Transparent and Secure Audio Steganography–An Innovative Approach

PDF) High capacity, transparent and secure audio steganography model based on fractal coding and chaotic map in temporal domain

Detecting and locating digital audio forgeries based on singularity analysis with wavelet packet | SpringerLink

Detecting and locating digital audio forgeries based on singularity analysis with wavelet packet | SpringerLink

PDF) High capacity, transparent and secure audio steganography model based on fractal coding and chaotic map in temporal domain

Detecting and locating digital audio forgeries based on singularity analysis with wavelet packet | SpringerLink









